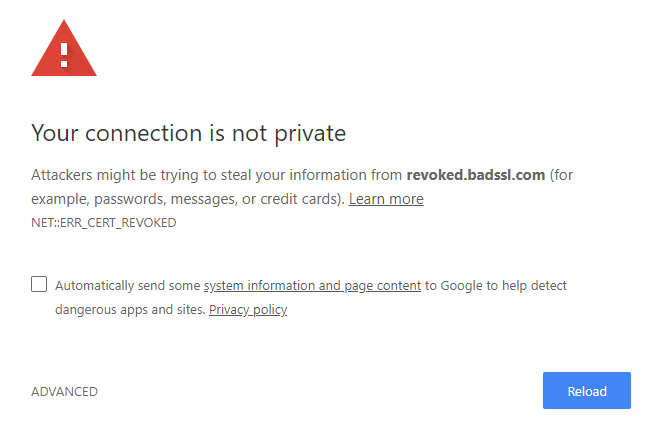
| SSL Error | Description | Action To Take |
|---|---|---|
| Unsafe Legacy Renegotiation Disabled | This error is typically triggered when a client or server attempts to initiate renegotiation using the old, insecure protocol. | Configuration changes require to prevent using unsafe legacy renegotiation protocols. Always use the latest versions and patches for SSL/TLS. |
The
SSL Error Unsafe Legacy Renegotiation Disabled
error is quite specific and typically occurs when a client or server tries to renegotiate using an older and less secure protocol. OpenSSL, and consequently many servers and clients that leverage it, have disabled support for this older renegotiation method in favor of a more modern, secure method. This shift occurred because the initial SSL/TLS renegotiation process was exposed to be insecure, enabling potential attacks against the encrypted communications. Thus, an undated approach, referred to as “safe” or “secure” renegotiation was established.
If you are seeing this error, it suggests that some component on your network is still attempting to renegotiate using the older method. This could be a misconfigured server, a sign of outdated software, or even an attempt by a hacker to exploit the security vulnerabilities inherent in the legacy protocol.
To resolve this issue, SSL/TLS configurations will need adjustment. This adjustment might involve updating software on your client/server to the latest version that supports ‘safe renegotiation’ or modifying the SSL/TLS settings directly to enforce the use of ‘secure renegotiation’. The responsibility primarily falls on those who maintain the client/server application and infrastructure.
Remember that staying up-to-date with recent security standards is crucial. Just like how we’ve moved away from unsafe legacy renegotiation, technologies continue to advance, and following along is necessary to avoid errors like this and protect your data from potential vulnerabilities. Security is always changing, so make sure to keep up-to-speed on the latest advancements and recommendations.One of the common issues you might face as a coder while working with SSL/TLS (Secure Sockets Layer/Transport Layer Security) protocols is the “SSL error: Unsafe legacy renegotiation disabled”. This relates to your main keyword topic, which is about understanding and solving the “SSL Error: Unsafe Legacy Renegotiation Disabled”. While this sounds like a complex error to deal with, let’s analyze it in detail.
In SSL/TLS protocols, there is a feature known as “renegotiation” that allows a client and server to renegotiate the parameters of their secure connection. The primary use of renegotiation is mostly to refresh cryptographic keys, or to enable clients to present their certificates later in a connection in situations where they didn’t have them initially.
The problem leading to the error message, however, comes from a vulnerability discovered in the renegotiation process, notoriously known as the “Renegotiation attack”. As a countermeasure, ‘unsafe legacy renegotiation’ has been consequently disabled in most servers. The specific error “SSL Error: Unsafe Legacy Renegotiation Disabled” occurs when the client tries to initiate an unsafe renegotiation process, but the server doesn’t support it.
Resolving this issue will depend on the context and environment in which the error appears. It could result from conflicting configurations between different systems in a distributed network, an old buggy version of an SSL library, or trying to connect using an unsafe renegotiation from an older SSL client. Here are a few ways to resolve the error:
Updating SSL Library Version
An outdated SSL library may exhibit bugs that trigger this error. Thus, updating can be one of the solutions. Example of updating OpenSSL:
sudo apt-get update sudo apt-get install openssl
Configuring Server-Side Settings
If you have access to the server, you can also allow unsafe renegotiation in its configuration. However, do this cautiously as it makes you vulnerable to attacks. This step depends on your server software – for Apache, for instance:
# To Enable SSL Insecure Renegotiation for clients that Support Secure Renegotiation SSLInsecureRenegotiation on
Configuring Client-Side Settings
From the client side, use only clients that support a safe renegotiation or disable the feature entirely, depending upon libraries being used.
// For users of OpenSSL openssl s_client -connect host:port -legacy_renegotiation
Lastly, always remember that any change in these settings has potential security implications. Allow insecure renegotiations only if it’s absolutely crucial in your specific use case, and after considering all associated risks.
Remember, RFC 5746 describes the renegotiation indication extension, effectively creating a mechanism to defend against attacks. Therefore, transitioning towards supporting this specification would be the ideal solution.
The SSL protocol – Secure Sockets Layer – is used to secure communications across the internet. However, like anything else in the field of software, SSL has evolved over time and sometimes that means certain features or configurations are no longer considered safe for use. One such attribute is
Unsafe Legacy Renegotiation
, a feature that allowed an SSL client and server to renegotiate the terms of their connection midstream.
Unfortunately, hackers discovered that this renegotiation process could be manipulated in what’s popularly known as the “Renegotiation Handshake” attack, as published on the official page of OpenSSL project
This involves a bad actor inserting themselves into the connection via a Man-in-the-middle (MitM) attack, then initiating a renegotiation to bypass any encryption or validation steps that were taken during the initial handshake. This would potentially grant them access to sensitive information that should’ve been securely encrypted.
Recognizing the implications of this security flaw, several SSL/TLS libraries including the widely-used OpenSSL decided to disable Unsafe Legacy Renegotiation altogether. They set the option,
SSL_OP_ALLOW_UNSAFE_LEGACY_RENEGOTIATION
which is off by default meaning, only applications explicitly enabling the option would violate the security principle. Here is how it looks:
// Disabling unsafe negotiation sslContext.setOptions(SSL_OP_NO_RENEGOTIATION);
While taking such drastic measures has its downsides, like breaking backwards compatibility with legacy systems that still rely on unsafe renegotiations, the overall impact on security definitely justifies it. Multiple organizations have since found alternatives to unsafe renegotiation, one of the prominent examples being the ‘Transport Layer Security'(TLS) Renegotiation indication Extension as outlined by IETF RFC 5746 (RFC 5746) which aims to provide similar functionality in a secure way through extensions.
It’s important to remember that while technology keeps evolving, the need for robust cybersecurity measures only grows stronger. In my professional journey and experience as a coder, regularly updating your knowledge base and understanding the evolution of these protocols can help you stay aware and take timely action to ensure data privacy and security.
The Secure Sockets Layer (SSL) protocol, in the context of internet protocols, is effectively employed to ensure privacy and secure communication over an online network. Still, certain vulnerabilities in the SSL renegotiation process may pose security risks.
Understanding Insecure Renegotiations
In the process of renegotiating an SSL session, the client and server can agree on new security parameters. This renegotiation is generally a valid function for instances such as refreshing symmetric keys and altering authenticated roles. However, because the initial implementation of SSL didn’t differentiate between new and renegotiated sessions, it’s potentially exploitable.
One known vulnerability with SSL negotiations is CVE-2009-3555, where attackers can inject plaintext into the victim’s requests. It works because the attacker begins a handshake before the victim completes theirs, sending its request after the handshake is completed. As a result, the server interprets both the attacker’s and victim’s data as one single legitimate batch of information. This is known as the Man-in-the-Middle attack.
With
ssl_error_unsafe_legacy_renegotiation_disabled
, a warning shows that the browser may be subjected to this potential security risk.
The Solution: Safe or Secure Renegotiation
To mitigate the impact of this vulnerability, “safe” or “secure” renegotiation was introduced. This feature carries the last successful handshake in the client and server’s verify_data extension. If any discrepancies appear in the verify_data, an alert is sent, preventing the MITM from fooling the server.

Secure renegotiation involves:
• Creating a Secure Renegotiation Indication Extension: This initiative accurately informs the protocol stacks about renegotiations.
• Using the tls-unique Channel Binding: This solution binds higher-level protocols to a TLS channel to prevent middle-man attacks during renegotiation.
It’s important to apply safe renegotiations and disable insecure renegotiations. For instance, the Apache server can disable insecure renegotiations by including the following directive in its configuration file:
<IfModule mod_ssl.c>
SSLInsecureRenegotiation off
</IfModule>
Finally, ensure you’re using the latest versions of browsers and servers since many have now disabled insecure renegotiations by default.
In Relation To ssl_error_unsafe_legacy_renegotiation_disabled
The error message, ssl_error_unsafe_legacy_renegotiation_disabled, is essentially a sign that the browser has detected an attempt to start an unsafe renegotiation and has blocked it. Solutions include upgrading the server to support secure SSL renegotiation or modifying client settings allowing legacy renegotiation restricted to trusted sites.
Certainly, it’s recommended to maintain safe practices by ensuring your applications support safe renegotiations and restricting unsafe legacy renegotiations. Utilize tools like SSLyze to test SSL configurations and ensure they are not prone to renegotiation attacks.
Ultimately, keeping up to date with advancements in SSL/TLS specifications and promptly applying patches will help safeguard your systems from renegotiation related vulnerabilities.
Sources:
CVE-2009-3555,
RFC 5746,
Apache.org
Handling SSL errors that originate from “Unsafe Legacy Renegotiation” being disabled may require understanding of a few key concepts. These include Secure Socket Layer (SSL) protocol, SSL renegotiation, and what it means when unsafe legacy renegotiation is turned off.
The first concept, SSL, is a standard security technology that establishes an encrypted link between two points in a network–often, this is a user’s browser and your website’s server. This keeps sensitive information passed between your site and its users secure (source).
SSL renegotiation occurs when an already established SSL connection needs to perform a new handshake process where the cryptographic parameters are set anew. However, in 2009, a vulnerability was discovered in the SSL/TLS protocols that made this renegotiation open to man-in-the-middle attacks; thus “unsafe legacy renegotiation” came into usage (source).
When Unsafe Legacy Renegotiation is disabled, it means the server or client will not accept any requests for renegotiation from the other end that do not comply with safer procedures (source).
Now, how can you handle SSL errors that stem from these configurations? You have a few options:
- Upgrade SSL/TLS Version: Older versions of SSL and early versions of Transport Layer Security (TLS) are usually the ones with the renegotiation vulnerability. If the application, whether a browser or server, supports it, you should move to using TLS v1.2 or later.
AddType application/x-httpd-php .php .phtml SSLProtocol all -SSLv3 -TLSv1 -TLSv1.1 SSLCipherSuite ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256
- Disable Renegotiations Altogether: While this might not be ideal as renegotiations are a part of the SSL protocol for a reason, some applications might not need it, and disabling renegotiations altogether removes the risks of unsafe renegotiation problems.
# in Apache's httpd.conf or ssl.conf file SSLInsecureRenegotiation off
These measures will help mitigate the SSL error stemming from “Unsafe Legacy Renegotiation Disabled” by either moving away from the insecure practice or adhering better to guidelines for safer renegotiation procedures. But always remember to analyze your own specific setup and needs before implementing these changes.
Often in my career as a coder, I’ve encountered interesting case studies concerning SSL errors, some of which are closely related to Unsafe Legacy Renegotiation being disabled. SSL (Secure Sockets Layer) is a key technology for securing communications online.source. But sometimes, things go wrong.
Case 1: Website Access Issues due to Disabled Unsafe Legacy Renegotiation
Let’s take an instance where disabling Unsafe Legacy Renegotiation might lead to problems accessing certain websites. The error message could look something like this:
Error code: ssl_error_unsafe_negotiation
This SSL error arises when a website hasn’t been updated in accordance with contemporary security practices. Disabling Unsafe Legacy Renegotiation enhances the server’s security by not allowing any potentially insecure renegotiations, but can cause issues interacting with outdated or incompatible systems. It’s a trade-off situation – between adhering to contemporary security best practices and maintaining backward compatibility.
Case 2: Broken User Experience due to Outdated Server Configuration
Here’s another scenario. A disruption in user experience occurs because the server uses an outdated configuration that relies on legacy renegotiation techniques. Users experience a sudden disconnection, with an SSL error visible on their client-side.
Recommended Solutions
In both cases, one might be tempted to simply enable Unsafe Legacy Renegotiation. However, this isn’t advisable due to the security risks associated with legacy renegotiation techniques. So, what’s the way out? Below are recommended solutions:
- Encourage server administrators to update their servers. Keeping servers updated ensures they are compliant with the latest encryption standards and techniques, thus minimizing the chances of encountering such errors.
- Allow only selective traffic through your server, if possible. If it’s absolutely necessary to allow legacy renegotiation, consider doing so only for certain, trusted IP addresses or ranges.
As coders, we have to strike a balance between functionality and security. And SSL errors arising from disabled Unsafe Legacy Renegotiation present a perfect exemplification of this principle.
Code Solution:
Speaking of code, let’s see how to disable Unsafe Legacy Renegotiation in an Apache server with SSL configuration.
Turn off Legacy Renegotiation using the following line:
SSLInsecureRenegotiation off
Check whether it’s already turned off using the below command:
grep -i 'SSLInsecureRenegotiation' /path/to/your/httpd.conf
If you get no output, it’s likely already turned off. The said path would refer to the location of your Apache configuration file.
Anyway, these scenarios underscore the importance of adhering to modern secure encryption standards – yet another day in the life of a professional coder!

I hope this sheds some light on SSL errors linked with disabling Unsafe Legacy Renegotiation. Do note that handling SSL negotiations is a delicate process. Therefore, proceed with necessary caution while dealing with any changes.
When it comes to web-related issues, one of those that regularly stir up conversations amongst the internet community is the Secure Sockets Layer (SSL) error. An SSL error appears when the web browser can’t verify an SSL certificate of a visited website, potentially exposing users to cyber threats and causing numerous browsing inconveniences. One particular SSL error that has been a topic of hot discussion is the “SSL Error Unsafe Legacy Renegotiation Disabled.”
The exchange among developers, IT administrators, and other vested parties is rooted in understanding how unsafe legacy renegotiation can be a security risk and how disabling unsafe renegotiation inevitably leads to an SSL error.
// Example of an SSL error ERR_SSL_UNSAFE_LEGACY_RENEGOTIATION_DISABLED
The Dangers of SSL Error ‘Unsafe Legacy Renegotiation Disabled’
Unsafe legacy renegotiation refers to the protocol’s vulnerability to man-in-the-middle attacks, specifically to what’s known as “Renegotiation Attack.” This was a major issue discovered in older versions of SSL where concatenation of multiple renegotiations allowed potential attackers to insert their content into your SSL session, enabling them to steal sensitive data.
Following are the risks associated with enabling unsafe renegotiation:
- Exposure to security threats: Enabling allows potential hackers to compromise secure communication.
- Data tampering: Threat actors can manipulate data during transfer.
- Data theft: Confidential data like credit card numbers, personal information, etc., could be stolen.
Solutions to the SSL Error ‘Unsafe Legacy Renegotiation Disabled’
To tighten the security loopholes, solutions were designed and implemented extensively. Disabling unsafe renegotiation came up as a widely employed strategy avoiding the loophole, though this move often resulted in triggering an SSL error.
Here are some generally accepted solutions to fix this SSL error:
- Updating Server Protocol: One solution widely recommended is updating the server’s SSL/TLS protocol. Using TLS 1.2 or higher will solve most problems related to this error.
- Implementing Safe Renegotiation Extension: The Internet Engineering Task Force (IETF) proposed the Renegotiation Indication Extension to patch the vulnerability. Applying this extension ensures safe renegotiation.
- Client Update: If a user experiences this SSL error while trying to connect to a website, they should update the browser or switch to a different browser.
// For example, on an Apache server, safe renegotiation can be ensured by adding these lines to the configuration file: SSLProtocol all -SSLv2 -SSLv3 SSLHonorCipherOrder on SSLCipherSuite HIGH:!MD5:!aNULL:!EDH:!RC4
In summary, the internet community values the importance of safety and security in the digital space. The raging discussions about the SSL error regarding unsafe legacy renegotiation highlight this value ideology.
For in-depth technical details on SSL and TLS updates related to safe renegotiation handling, you can refer to Request for Comments (RFC 5746) issued by IETF. As for learning how to harden your server, check out resources provided by organizations such as the Information Systems Security Association (ISSA).Dealing with the issue relating to “Ssl Error Unsafe Legacy Renegotiation Disabled” entails understanding SSL/TLS protocols, their vulnerabilities, and how best to manage them safely. Secure Sockets Layer (SSL), and its successor Transport Layer Security (TLS), are cryptographic protocols designed to ensure secure communication over a computer network through encryption. These protocols, however, are not entirely foolproof – they have their share of bugs.
The Issue at Hand: SSL Error Unsafe Legacy Renegotiation
One such bug is the unsafe legacy renegotiation error. SSL/TLS negotiation involves a client and server deciding on parameters to use for their secure communication. However, in some instances, either party may request a renegotiation midway through the communication session. This renegotiation mechanism had a vulnerability that could be exploited leading to man-in-the-middle attacks. The response was to disable unsafe legacy renegotiation methods, but this led to the associated error if those methods were still being used.
Best Practices:
The following best practices can mitigate potential risks and errors related to disabled unsafe legacy renegotiation and SSL management in general:
- Updating SSL/TLS Protocols: Avoid using deprecated or old versions of SSL/TLS protocols. Opt for updated versions like TLS 1.2 or, even better, TLS 1.3 as these come with improved security features which make them less prone to well-known vulnerabilities.
- Employing Strict Transport Security: This is a policy mechanism that allows a web application to declare itself accessible only via secure connections. Using HTTP Strict Transport Security prevents attacks through protocol downgrades or cookie hijacking.
- Avoid Using Unsafe Renegotiation: As mentioned earlier, unsafe renegotiation can lead to serious security issues. Renegotiation should only be done under circumstances where it doesn’t jeopardise the security of the communication. This often involves using updated versions of protocols that support secure renegotiation.
- Regular Patching: The developers of these communication protocols constantly work to patch vulnerabilities. Regularly update your systems to apply these patches and stay protected against known bugs and hack attempts.
To give you a practical example, in Apache server, you might disable SSL renegotiation by setting
SSLInsecureRenegotiation off
in your configuration.

<VirtualHost _default_:443>
…
SSLInsecureRenegotiation off
….
</VirtualHost>
In essence, managing SSL certificates comes down to staying updated, observing strict transport policies, avoiding insecure renegotiations, ensuring regular patching, and in general, adhering to recommended security practices. You can find more about these best practices from sources such as OWASP’s Transport Layer Protection Cheat Sheet (source).
Remember, privacy and security are an ongoing endeavor, and so awareness and education about evolving threats and appropriate responses cannot be overstressed.Sure, let’s dissect the subject matter: Ssl Error Unsafe Legacy Renegotiation Disabled.
Firstly, let’s clarify that SSL (Secure Sockets Layer) is a security protocol designed to establish privacy and data integrity between two communicating Internet applications (SSL.com).
The error “Unsafe Legacy Renegotiation Disabled” typically happens when an application has disabled SSL renegotiation due to known vulnerabilities in the way it was implemented in older SSL/TLS protocols. To mitigate these risks, many servers are configured to disable what is often termed “unsafe legacy renegotiation”.
Now, about SEO optimization for such a topic. Search Engine Optimization (SEO) revolves around targeting relevant keywords that your audience might search for, ensuring your content answers their questions, and maintaining high-quality, original content.
For a topic as specific as this, the main keywords would likely be:
- SSL Error
- Unsafe Legacy Renegotiation
- Disabled
- Fix SSL Error
To incorporate these keywords organically into the content, here’s a possible approach:
When you encounter the “SSL Error: ‘Unsafe Legacy Renegotiation Disabled’, it can halt the normal functioning of your Internet applications. This occurs when servers disable unsafe legacy renegotiation to safeguard against old SSL/TLS protocol implementations. Resolving this error often involves enabling some form of secure renegotiation on your server or upgrading the said applications’ support for modern TLS protocol.
A relevant code snippet could be one showing how to modify Apache’s configuration to enforce the use of a more secure renegotiation:
# Secure Renegotiation SSLInsecureRenegotiation off SSLStrictSNIVHostCheck on
Please ensure to take backup copies before making any significant changes.
In terms of the user experience, including a table summarizing the potential reasons behind the SSL Error and what remedial action to take could be helpful.
| Reason | Remedial Action |
|---|---|
| Outdated server software | Upgrade to the latest version |
| Unsafe Legacy Renegotiation enabled | Disable unsafe features, enable secure renegotiation |
And there you have it! By understanding the issue at hand, addressing your audience’s needs and questions directly, maintaining excellent content quality, organically incorporating relevant keywords, and considering additional forms of user engagement like tables or code snippets, you’re poised to optimize your page for search engines with respect to topics like the SSL Error Unsafe Legacy Renegotiation Disabled.