In the fast-paced world of software development, delivering high-quality, secure, and maintainable code is paramount. While manual code reviews and dynamic testing are crucial, they often occur late in the development cycle. Static analysis, a powerful form of automated code analysis, shifts this process left, enabling teams to identify bugs, security vulnerabilities, and style issues directly within the development workflow. This proactive approach not only saves time and resources but also fosters a culture of quality and security from the very first line of code. This article explores the fundamentals of static analysis, its practical implementation, and how cutting-edge advancements, including Artificial Intelligence, are revolutionizing its effectiveness and transforming modern Software Debugging.
The Foundations of Static Analysis
Static analysis, often referred to as Static Application Security Testing (SAST) in a security context, is the process of analyzing source code, byte code, or application binaries for potential issues without actually executing the program. This stands in contrast to Dynamic Analysis, which tests an application while it is running. By examining the code’s structure and logic, static analysis tools can uncover a wide range of problems that might otherwise go unnoticed until production.
How Does Static Analysis Work?
At its core, static analysis involves several key steps. First, the tool parses the source code to build an internal representation, most commonly an Abstract Syntax Tree (AST). An AST is a tree-like structure that represents the grammatical and logical flow of the code. Once the AST is built, the analysis engine traverses this tree, applying a predefined set of rules or heuristics to identify patterns that indicate potential errors, vulnerabilities, or deviations from coding standards.
These rules can detect various categories of issues, including:
- Code Quality and Maintainability: Identifying overly complex functions (high cyclomatic complexity), unused variables, dead code, and inconsistent formatting.
- Security Vulnerabilities: Detecting common weaknesses like SQL injection, Cross-Site Scripting (XSS), buffer overflows, and insecure use of cryptographic APIs.
- Bug Detection: Finding potential null pointer dereferences, resource leaks, and race conditions.
- Style and Convention Violations: Enforcing team-specific or language-specific coding standards to ensure consistency across the codebase.
A Simple Example: Detecting Hardcoded Secrets
Imagine a developer accidentally hardcodes an API key in their Python code. A static analysis tool can be configured with a rule to detect high-entropy strings or specific patterns that resemble keys. This simple check prevents sensitive credentials from being committed to version control, a common and dangerous security mistake.
# main.py
import requests
def get_user_data(user_id):
# This hardcoded key would be flagged by a static analysis tool.
api_key = "ak_live_aHR0cHM6Ly93d3cueW91dHViZS5jb20vd2F0Y2g"
headers = {
"Authorization": f"Bearer {api_key}",
"Content-Type": "application/json"
}
response = requests.get(f"https://api.example.com/users/{user_id}", headers=headers)
if response.status_code == 200:
return response.json()
else:
# Proper error handling should be implemented here
return None
# A static analysis rule would identify the 'api_key' variable as a potential secret.
# The rule might use regex to look for common key prefixes ('ak_live_') or
# analyze the string's entropy to flag it as a likely credential.In this Python Development scenario, the tool isn’t running the code; it’s simply reading it and matching patterns. This is the essence of static Code Analysis and a fundamental step in proactive Bug Fixing.
Integrating Static Analysis into Your Development Workflow
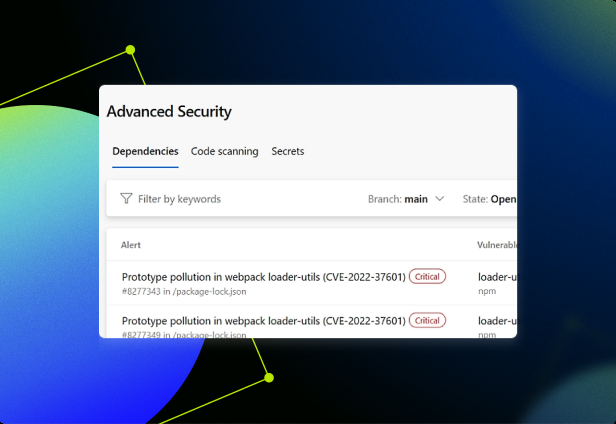
Code scanning for vulnerabilities – GitHub Advanced Security in Azure DevOps for Safer Code
The true power of static analysis is unlocked when it becomes an integral, automated part of the development lifecycle. Integrating these Developer Tools into your CI/CD pipeline and local development environment provides immediate feedback, making it easier and cheaper to fix issues.
Choosing the Right Tools
The market is filled with excellent static analysis tools, both open-source and commercial, tailored for different languages and ecosystems. Some popular choices include:
- JavaScript/TypeScript: ESLint, JSHint, Prettier (for formatting)
- Python: Pylint, Flake8, Bandit (for security), Black (for formatting)
- Java: SonarQube, Checkstyle, PMD
- Multi-language Platforms: SonarQube, Snyk, Veracode, Checkmarx
When selecting a tool, consider factors like language support, rule customizability, integration capabilities (e.g., with GitHub, Jenkins, VS Code), and the specific types of issues you want to prioritize (e.g., security, performance, or style).
Automating with CI/CD and Git Hooks
Automating static analysis ensures that no code reaches the main branch without meeting a minimum quality and security bar. This is a key practice in modern CI/CD Debugging.
1. Pre-commit Hooks: By using a framework like pre-commit, you can run linters and formatters automatically before a developer even creates a commit. This catches issues at the earliest possible stage.
# .pre-commit-config.yaml
# This configuration runs the Black formatter and Flake8 linter on any modified Python files.
repos:
- repo: https://github.com/psf/black
rev: 23.11.0
hooks:
- id: black
- repo: https://github.com/pycqa/flake8
rev: 6.1.0
hooks:
- id: flake82. Continuous Integration (CI) Pipelines: For more comprehensive checks, integrate static analysis into your CI pipeline using platforms like GitHub Actions, GitLab CI, or Jenkins. This step can act as a quality gate, failing the build if critical issues are detected.
# .github/workflows/linter.yml
# This GitHub Actions workflow runs ESLint on every pull request to the main branch.
name: JavaScript Linter
on:
pull_request:
branches: [ main ]
jobs:
lint:
name: Run ESLint
runs-on: ubuntu-latest
steps:
- name: Check out Git repository
uses: actions/checkout@v3
- name: Set up Node.js
uses: actions/setup-node@v3
with:
node-version: '18'
cache: 'npm'
- name: Install dependencies
run: npm ci
- name: Run ESLint
run: npm run lintThis level of Debug Automation provides a consistent safety net, crucial for maintaining code health in collaborative projects.
Advanced Techniques: Taint Analysis and the AI Revolution
While basic static analysis is excellent for finding localized issues, more advanced techniques are needed to trace complex vulnerabilities. Furthermore, the industry is tackling one of the biggest challenges of static analysis: the high rate of false positives.
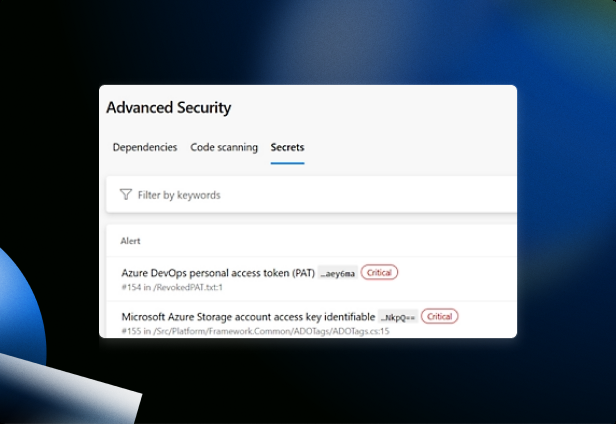
Code scanning for vulnerabilities – GitHub Advanced Security in Azure DevOps for Safer Code
Taint Analysis: Following the Data Flow
Taint analysis, or data flow analysis, is a sophisticated technique used to track untrusted data through an application. It works by marking data from external sources (e.g., user input from an HTTP request) as “tainted.” The analysis then follows this tainted data as it moves through the code. If the tainted data is ever used in a sensitive operation (a “sink”), such as a database query or an HTML response, without being properly sanitized, the tool raises an alarm.
This is extremely effective for finding vulnerabilities like SQL injection and XSS. Consider this Java snippet for a potential SQL injection vulnerability.
// A simplified Java Servlet example
import java.sql.Connection;
import java.sql.ResultSet;
import java.sql.Statement;
import javax.servlet.http.HttpServletRequest;
public class UserDAO {
public void getUserProfile(HttpServletRequest request, Connection connection) throws Exception {
// 1. Source: User input is retrieved from the request and is considered "tainted".
String username = request.getParameter("username");
// 2. Flow: The tainted 'username' string is concatenated directly into a SQL query.
String query = "SELECT * FROM users WHERE username = '" + username + "'";
Statement statement = connection.createStatement();
// 3. Sink: The query containing tainted data is executed against the database.
// A taint analysis tool would flag this line as a SQL injection vulnerability.
ResultSet resultSet = statement.executeQuery(query);
// ... process results
}
}A taint-aware static analysis tool would identify that username is a tainted source and that statement.executeQuery(query) is a sensitive sink. By tracing the data flow, it correctly flags this as a high-risk security flaw, a critical part of modern API Debugging and Backend Debugging.
The Challenge of False Positives and the AI Solution
A long-standing criticism of static analysis tools is their tendency to generate a high volume of “false positives”—warnings about issues that aren’t actually problems. This noise can lead to “alert fatigue,” where developers start ignoring the tool’s output altogether. The root cause is that traditional, rule-based systems lack a deep understanding of the code’s context and intent.
This is where Artificial Intelligence, specifically Large Language Models (LLMs), is creating a paradigm shift. By combining traditional static analysis with the contextual understanding of an LLM, a new generation of tools can dramatically reduce false positives. The process typically works as follows:

Code scanning for vulnerabilities – How to Scan a Website for Vulnerabilities (6 Tools)
- Initial Scan: A traditional static analysis engine performs its scan, identifying a list of potential vulnerabilities.
- AI-Powered Triage: For each finding, the relevant code snippet, the warning message, and surrounding code context are passed to a fine-tuned LLM.
- Contextual Analysis: The LLM analyzes the code’s logic, variable names, and comments to understand the developer’s intent. It can determine if a variable flagged as “tainted” has actually been validated through a custom sanitization function that the traditional scanner missed, or if a seemingly dangerous operation is safe within the specific context of the application.
- Filtering and Prioritization: Based on its analysis, the LLM classifies each finding as a true positive, a likely false positive, or provides additional context to help the developer make a decision.
This hybrid approach leverages the speed and breadth of traditional scanners with the deep, nuanced understanding of AI, leading to more accurate, actionable results and making Error Tracking far more efficient.
Best Practices for Effective Static Analysis
To get the most out of static analysis without overwhelming your team, follow these best practices:
- Start Small and Iterate: When introducing a tool to a legacy codebase, don’t enable all rules at once. Start with a small, high-impact set of rules (e.g., critical security flaws) and gradually expand as you clean up the code.
- Customize Your Rule Set: Every project is different. Fine-tune the tool’s configuration to align with your team’s coding standards and priorities. Disable rules that are not relevant to your project to reduce noise.
- Integrate into the IDE: Provide developers with real-time feedback by integrating static analysis tools directly into their code editors (like VS Code or IntelliJ). This is a core tenet of effective JavaScript Development and Python Development.
- Establish a Baseline: For existing projects, establish a baseline of current issues. Configure your CI/CD pipeline to fail only on new issues, allowing you to address the existing technical debt over time.
- Educate and Empower: Ensure developers understand the “why” behind the rules. Provide documentation and training on common issues and how to fix them correctly. This turns static analysis from a punitive gate into a valuable learning and Debugging Tool.
Conclusion
Static analysis has evolved from a niche tool for quality purists into a foundational pillar of modern software development and security. By automating the detection of bugs and vulnerabilities early in the lifecycle, it empowers teams to build more robust and secure applications efficiently. The integration into CI/CD pipelines has made it a seamless part of the daily workflow, while advanced techniques like taint analysis uncover deep-seated security flaws.
Looking ahead, the fusion of static analysis with AI is set to solve its biggest historical challenge: the noise of false positives. By adding contextual intelligence, these next-generation tools promise to deliver highly accurate, prioritized, and actionable insights, allowing developers to focus on what truly matters. Whether you are just starting or looking to enhance your current setup, embracing a robust static analysis strategy is one of the most impactful investments you can make in your codebase’s long-term health and security.